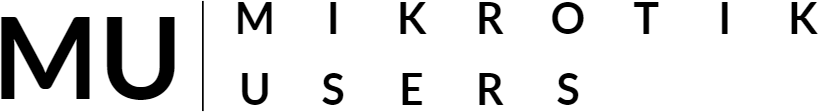Lab 3.1 Firewall Workshop
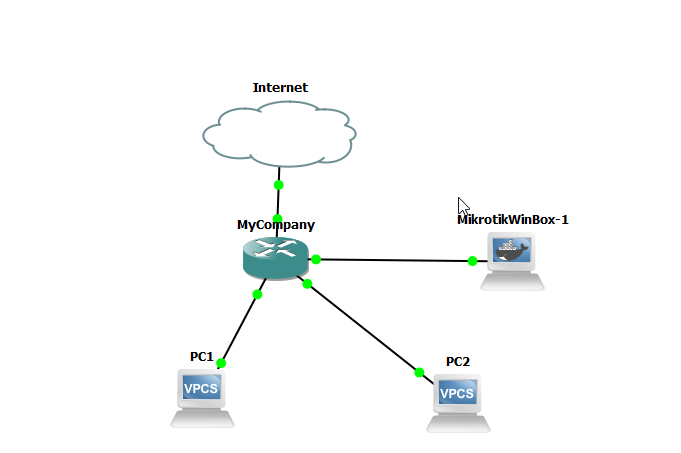
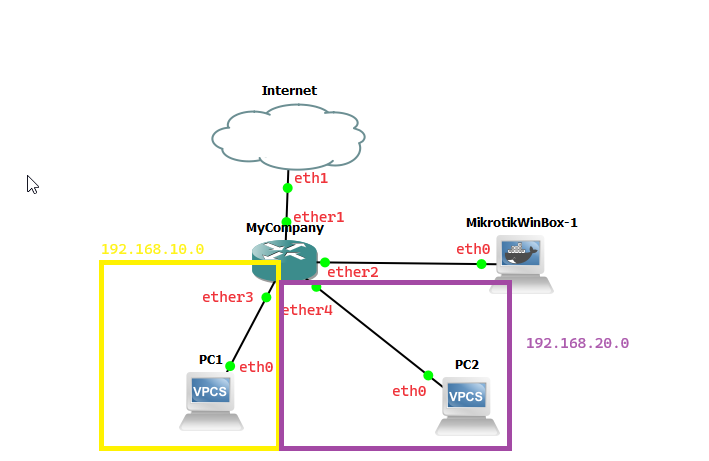
For this lab, we are going to create the following GNS topology. In this scenario, PC1 belongs to department 1 and PC2 belongs to department 2 and we want to set up a firewall to prevent PC1 from being able to connect to the network that PC2 is on and vice-versa. For this scenario, we have added the MikroTik CHR cloud router, 2 VPCS machines, and the MikroTik WinBox appliance to our workspace.
Step 1: Add all the appliances to the workspace and create the links between the devices as shown above. If you need a refresher on how to add appliances to the workspace or create links for the devices, please view the following documentation here.
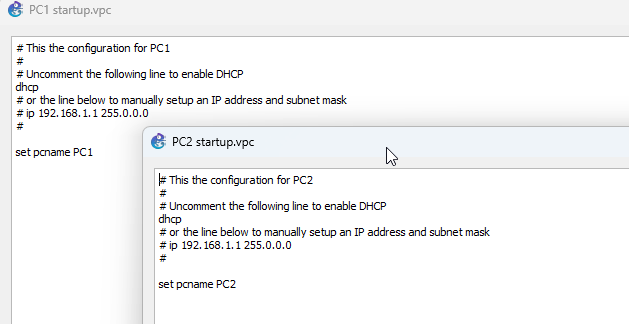
Step 2: Edit the configuration for PC1 and PC2 and set them both to DHCP. (Right click the appliance and Edit Config). Uncomment the dhcp line to enable DHCP.
Step 3: Start the CHR and MikrotikWinbox appliances. After the appliances have been started, right click the MikrotikWinBox appliance and select Console to launch the UI. When the appliance has been loaded, log into the device (you may have to use the IP6 address to log into the interface as I've noticed an issue sometimes using the MAC address with the CHR to log in. You can get the IP address from the Neighbors tab)