Lab 3.1 Creating a Basic Firewall with MikroTik Router - Part 3
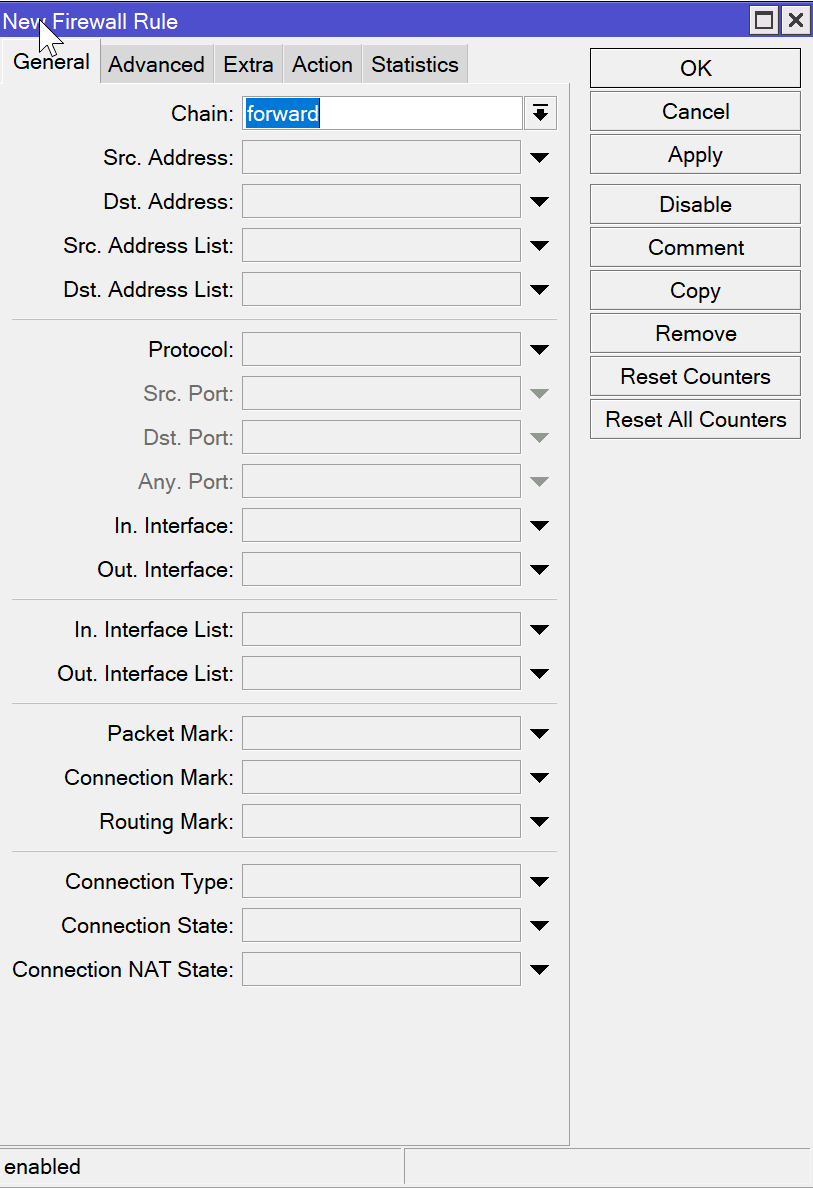
What is the chain and how does it work? It specifies the type of rule we are applying.
On a MikroTik router, understanding the differences between input, forward, and output firewall rules is crucial for managing network traffic effectively:
Input Rules: Input rules apply to traffic destined for the router itself. These rules control which packets are accepted by the router for services running on the router itself, such as management services (SSH, Telnet, Winbox), DNS resolution (if the router is acting as a DNS client or server), or services like SNMP (Simple Network Management Protocol).
- Example: If you have a rule in the input chain to accept SSH connections (TCP port 22), it allows traffic to the router itself on port 22.
Forward Rules: Forward rules apply to packets that are passing through the router. These rules govern traffic that is being routed from one network segment to another through the router. This includes packets that are being forwarded from one interface to another.
- Example: If your MikroTik router is routing traffic between two local networks (say, LAN and DMZ), forward rules will dictate what traffic is allowed or denied between these networks.
Output Rules: Output rules apply to traffic generated by the router itself. These rules control which packets generated by the router are allowed to leave the router to reach their destination.
- Example: Outgoing traffic initiated by the router, such as DNS queries, NTP requests, or responses to internal requests, are controlled by output rules.
Key Differences:
Destination of Traffic:
- Input: Traffic destined for the router itself.
- Forward: Traffic passing through the router.
- Output: Traffic generated by the router.
Direction of Traffic Flow:
- Input: Traffic flowing towards the router.
- Forward: Traffic passing through the router from one interface to another.
- Output: Traffic flowing away from the router, generated by the router itself.
Typical Use Cases:
- Input: Securing access to router management services.
- Forward: Controlling traffic between different networks.
- Output: Managing traffic leaving the router.
Src. Address (Source Address):
- Defines the source IP address or network range for incoming packets that will match the rule. Use
!for negation (not).
Dst. Address (Destination Address):
- Defines the destination IP address or network range for outgoing packets that will match the rule. Use
!for negation (not).
Protocol:
- Specifies the protocol (TCP, UDP, ICMP, etc.) that the rule will match. Use
allfor any protocol.
Src. Port (Source Port):
- Defines the source port number or range of port numbers that incoming packets must match to trigger the rule. Use
!for negation (not).
Dst. Port (Destination Port):
- Defines the destination port number or range of port numbers that outgoing packets must match to trigger the rule. Use
!for negation (not).
Action:
- Specifies what action to take when a packet matches the rule criteria:
accept: Allow the packet.drop: Silently discard the packet.reject: Discard the packet and notify the sender with an error message.
Comment:
- Allows you to add a description or note for the rule, which can be helpful for documentation and management purposes.