Staying Safe Online: Enabling Secure Access to an Internal Network with OpenVPN

First lets begin by explaining what OpenVPN is and why you would use it. Then we'll look at some common scenarios and then cover setup of OpenVPN on our MikroTik router and client installation and deployment.
So what is OpenVPN.
OpenVPN is a virtual private network (VPN) application service (server and client) which provides a securely encrypted Internet connection to your private network over the public Internet. It allows devices to connect to insecure networks (think Internet cafes, coffee shops, public Wi-Fi hotspots) but then layers a secure bridge on top of them that allows you to pass data safely and securely between them without worrying about the data or the device being compromised.
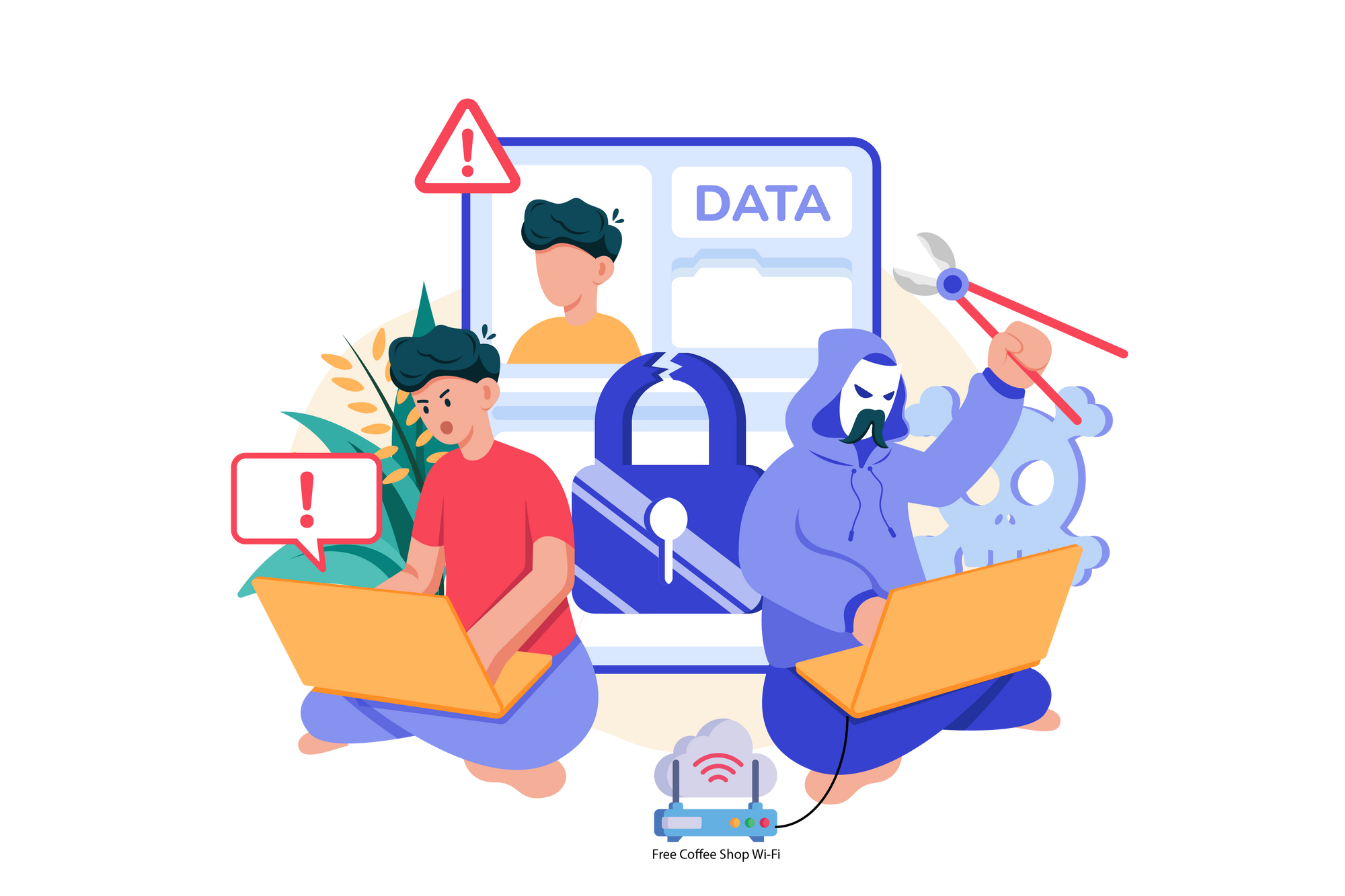
For example, think of the scenario where you connect to your local coffee shops free Wi-Fi. You are then relying on the coffee shop to ensure the security of your data and your connection. However, it is completely possible for a bad actor (a.k.a. hacker) to also be connected to the same Wi-Fi hotspot and compromise the security of that public Wi-Fi and intercept, redirect, or even manipulate your online connection. Some bad actors may even set up free public Wi-Fi access points themselves in the hopes of luring unsuspecting victims into scenarios where the above most certainly will occur. You could be redirected to malicious websites, have your information stolen, have your device compromised or even more.
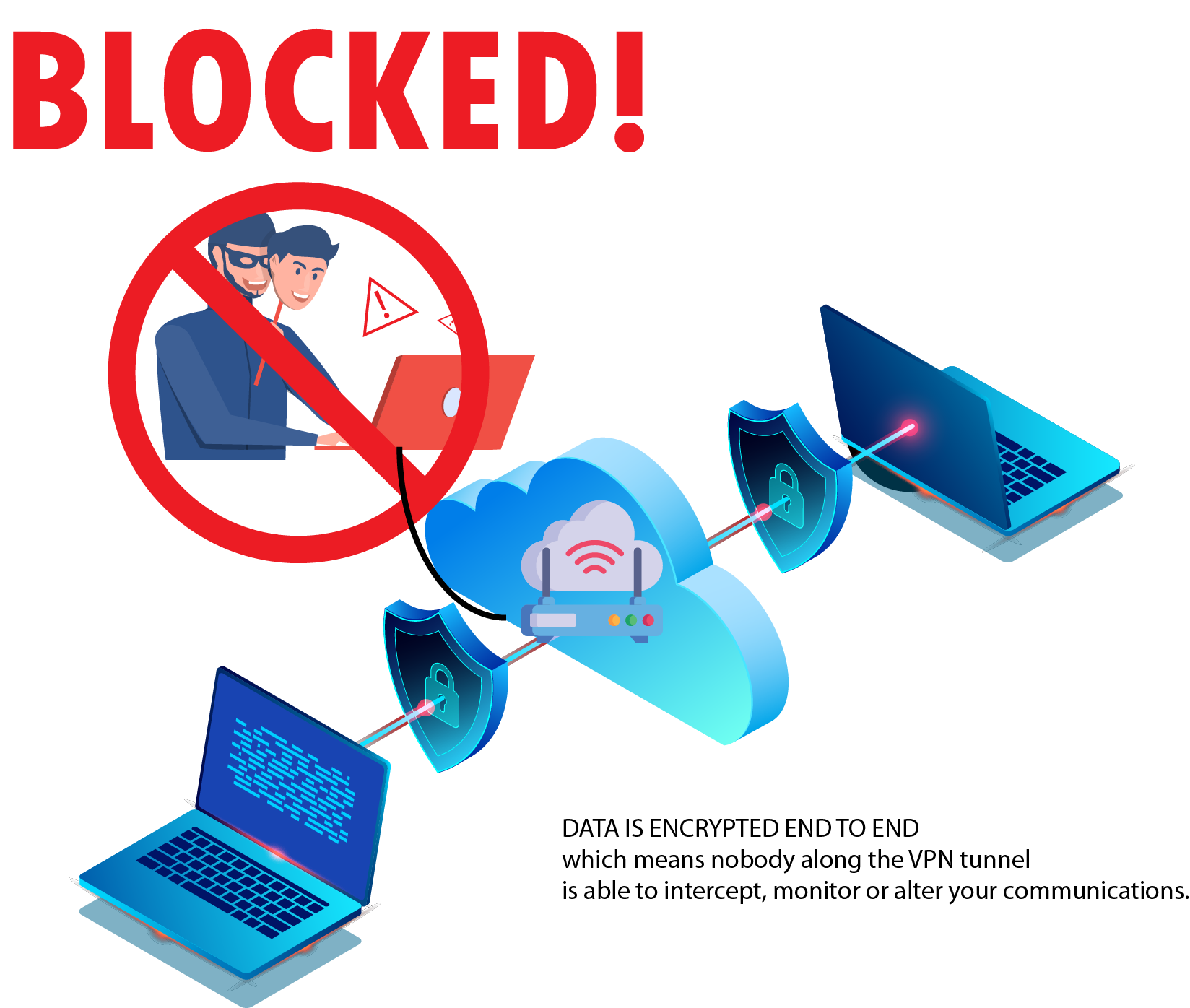
A VPN hides your IP address and encrypts your online activity by connecting you to an encrypted, private VPN server. Your data then passes through that VPN server and onto the internal network and/or the Internet. By doing this, you can establish a secure connection between your device and the internal devices on the internal network, such as a printer, gaming device, servers, etc. as well as provide a secure connection to the Internet. Certificates verify the authenticity of the VPN server you are connecting to. If someone attempts to imitate the server without the proper certificate, you will not be allowed to connect and also notified that the connection attempt failed because the server that was expected could not be properly verified. You should really be using a VPN anytime you connect to public Wi-Fi to ensure your data is safe, especially if you are doing sensitive things such as accessing email, banking or shopping on the Internet.
In this tutorial we are going to be setting up a MikroTik router to act as our OpenVPN server. Devices will then be allowed connect to the server and data will pass over our encrypted connection and onto our private network and/or the Internet. Anytime we connect to an insecure network and connect to our VPN, all that insecure network will be allowed to see is the encrypted traffic. Our actual data remains safely hidden in our encrypted tunnel.