Lab 5.2 Configuring SSTP Site-to-Site VPN
In part 2 of our series, we delve into the configuration of SSTP, or Secure Socket Tunneling Protocol, which is considered a much safer method of encrypting traffic between two endpoints as opposed to PPTP. We are going to use a similar setup as to our previous example configuring PPTP. It is just as easy to set up SSTP as was PPTP, and SSTP should be considered the preferred method over PPTP.
What is SSTP?
SSTP, or Secure Socket Tunneling Protocol, is a VPN (Virtual Private Network) protocol developed by Microsoft. It’s designed to secure communications between a client and a server by tunneling communication through HTTPS (HTTP over SSL/TLS), which is the same encryption technology used for secure web browsing.
Key Features of SSTP:
- Encryption and Security: SSTP uses SSL/TLS for encryption, which is a robust and widely trusted method. This provides a high level of security, protecting data from eavesdropping and tampering.
- Firewall and NAT Traversal: Because SSTP uses HTTPS, it can easily pass through firewalls and Network Address Translation (NAT) devices, which can sometimes block other VPN protocols.
- Authentication: It supports strong authentication methods, including the use of certificates and username/password combinations.
Why SSTP is Preferred Over PPTP:
- Security: SSTP is generally considered more secure than PPTP (Point-to-Point Tunneling Protocol). PPTP has known security vulnerabilities and is susceptible to various attacks, whereas SSTP benefits from the strong encryption provided by SSL/TLS.
- Firewall and NAT Compatibility: SSTP can traverse firewalls and NAT devices more effectively than PPTP, which sometimes struggles with such network configurations.
- Data Integrity: SSTP ensures data integrity through SSL/TLS, reducing the risk of data corruption or manipulation during transmission.
- Modern Standards: SSTP aligns with modern security standards and practices, making it a more robust choice for secure communications compared to the outdated and less secure PPTP.
Overall, SSTP is a preferred choice for secure VPN connections on a MikroTik router or any other networking hardware due to its strong encryption, better firewall compatibility, and more modern security features compared to PPTP.
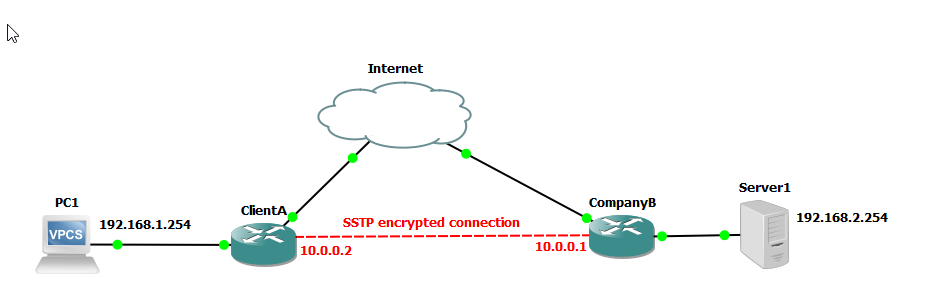
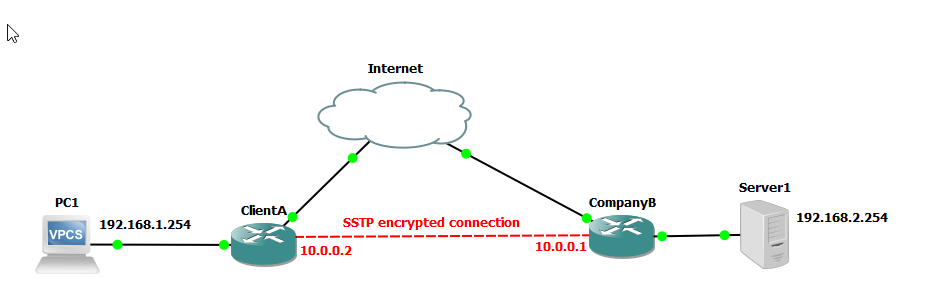
We are going to use the following network to demonstrate setup of a SSTP network. This is similar to the network we set up in a previous example using PPTP.