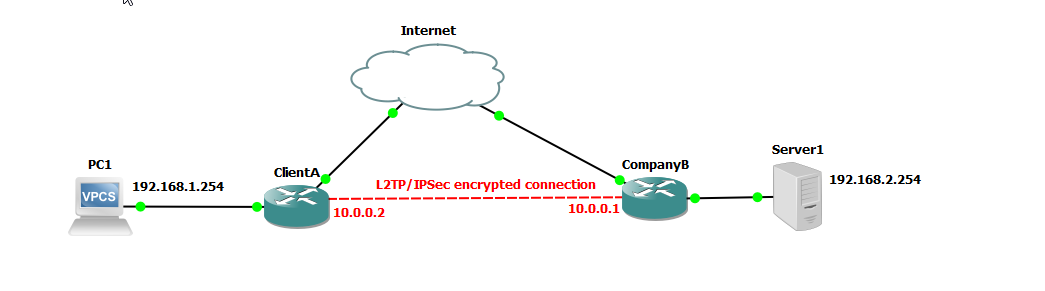
Lab 5.3 Configuring L2TP/IPSec Site-to-Site VPN
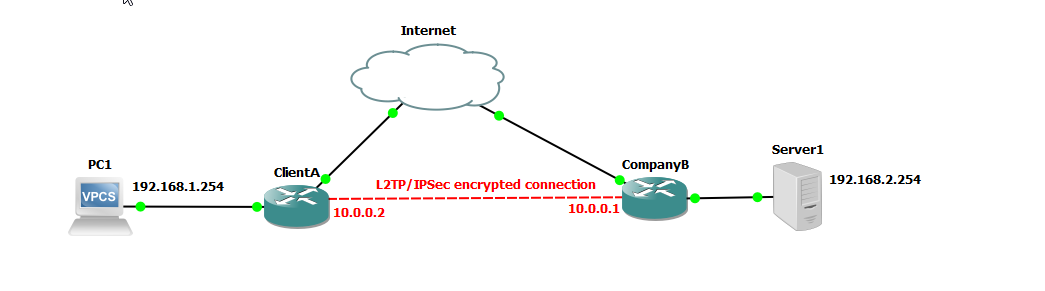
In part 3 of our series, we delve into the configuration of L2TP/IPSec (Layer 2 Tunneling Protocol with Internet Protocol Security), which is also considered a safe method of encrypting traffic between two endpoints. L2TP/IPsec is versatile and secure but may require more complex configuration and can face issues with firewalls and NAT because it uses UDP ports and IPsec protocols that may need special handling as opposed to SSTP which operates over TCP port 443 which is commonly open and used for HTTPS traffic. Choosing between L2TP/IPsec and SSTP depends on your specific needs, including the operating systems in use, network infrastructure, and security requirements.
We are going to use a similar setup as to our previous example configuring PPTP and SSTP.