Configuring Firewall Rules for VPN

The last part of this lab we look at configuring the firewall rules for our VPN setup. We set up routers for PPTP, SSTP, and L2TP/IPSec.
We are going to start with our default firewall rules. This setup allows us to start with a basic, albeit secure setup for our firewall. Apply the default firewall script to both routers in each scenario. What should occur is that we should no longer be able to connect from client to server, because what we have done is effectively closed the ports responsible for establishing communication between the two routers.
After applying the default firewall configuration rules, you should notice that your VPN traffic is still being sent thru. Why?
Well, if you look at the default firewall rule list, you will notice the following line.
filter add chain=input action=accept connection-state=established,related,untracked comment="defconf: accept established,related,untracked"
The main purpose of this rule is to ensure that established connections and related traffic can flow freely to the router. This is essential for maintaining active connections and allowing users to communicate with external servers without interruption.
When you set up a VPN, it typically creates an established connection once the VPN handshake and authentication processes are completed successfully. Here’s how it works:
VPN Connection Process
- Initial Connection: When a client attempts to connect to the VPN server, it sends a connection request. This is not yet an established connection.
- Authentication and Handshake: The client and server perform a handshake process, which includes authentication. During this stage, keys are exchanged, and the secure tunnel is established.
- Established Connection: Once the handshake is successful, the VPN tunnel is created, and the connection is considered established. At this point, any data packets sent between the client and the server are part of this established connection.
Impact on Firewall Rules
- Connection States: As the VPN connection is established, any subsequent traffic sent over that VPN tunnel (like data packets) would be classified as "established" traffic. This means that a firewall rule allowing established connections would permit this traffic.
- Related Traffic: If the VPN connection initiates additional connections (like accessing resources on the internal network), those would be considered "related" connections and would also be allowed by the firewall rule.
Once your VPN is successfully established, it falls under the "established" connection state, and the firewall rule above would allow that traffic without issues. In order to test the specific ports for firewall traffic, we need to temporarily disable the rule in order to prevent it from allowing the traffic to pass through uninhibited.
To do so, we are going to disable the firewall rule on our routers. At the console, enter the following command(s):
/ip/firewall/filter print
We do this one just to make sure we find the right rule to disable.
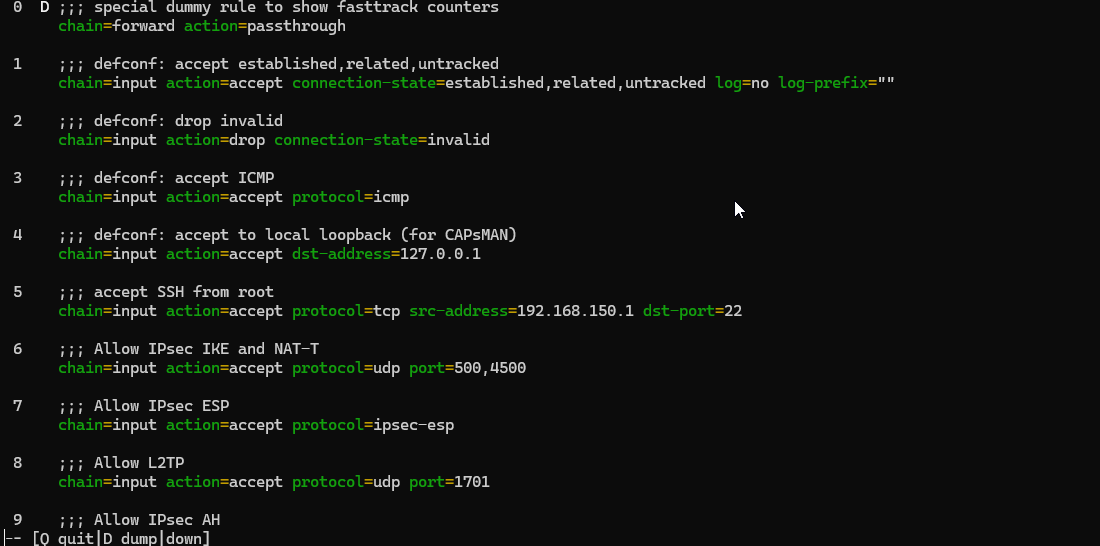
In our specific case, the firewall rule is #1, so to disable it we issue the following command.
/ip/firewall/filter disable 1
If you now try to ping from our PC1 to the Server, you will notice that the ping fails.
In order to re-establish the communication between the routers, we need to open specific ports to allow communication. In our previous examples, we had two routers, ClientA and CompanyB, with IP addresses of 192.168.150.146 for the client, and 192.168.150.147 for the server network.
Let's look at the changes we would need to make in order to re-establish communication on a PPTP network.
PPTP Firewall Setup
IP Firewall changes on Company B
Generic (allow PPTP from any host)
/ip firewall filter
add chain=input protocol=tcp port=1723 action=accept comment="Allow PPTP control connection"
add chain=input protocol=gre action=accept comment="Allow GRE for PPTP"
OR
Specific (create a specific inclusion rule for Client A)
/ip firewall filter
add chain=input protocol=tcp port=1723 src-address=192.168.150.146 action=accept comment="Allow PPTP from Client A"
add chain=input protocol=gre action=accept comment="Allow GRE for PPTP"
- The first rule allows all incoming TCP traffic on port 1723, which is the PPTP control connection port.
- The second rule allows all incoming GRE traffic, which is necessary for PPTP connections. GRE, or Generic Routing Encapsulation, is a tunneling protocol developed by Cisco that is used to encapsulate a wide variety of network layer protocols into a point-to-point connection. GRE (Generic Routing Encapsulation) is used by PPTP for encapsulating data.
- The third rule allows incoming TCP traffic on port 1723 only if it originates from the IP address of our other router.
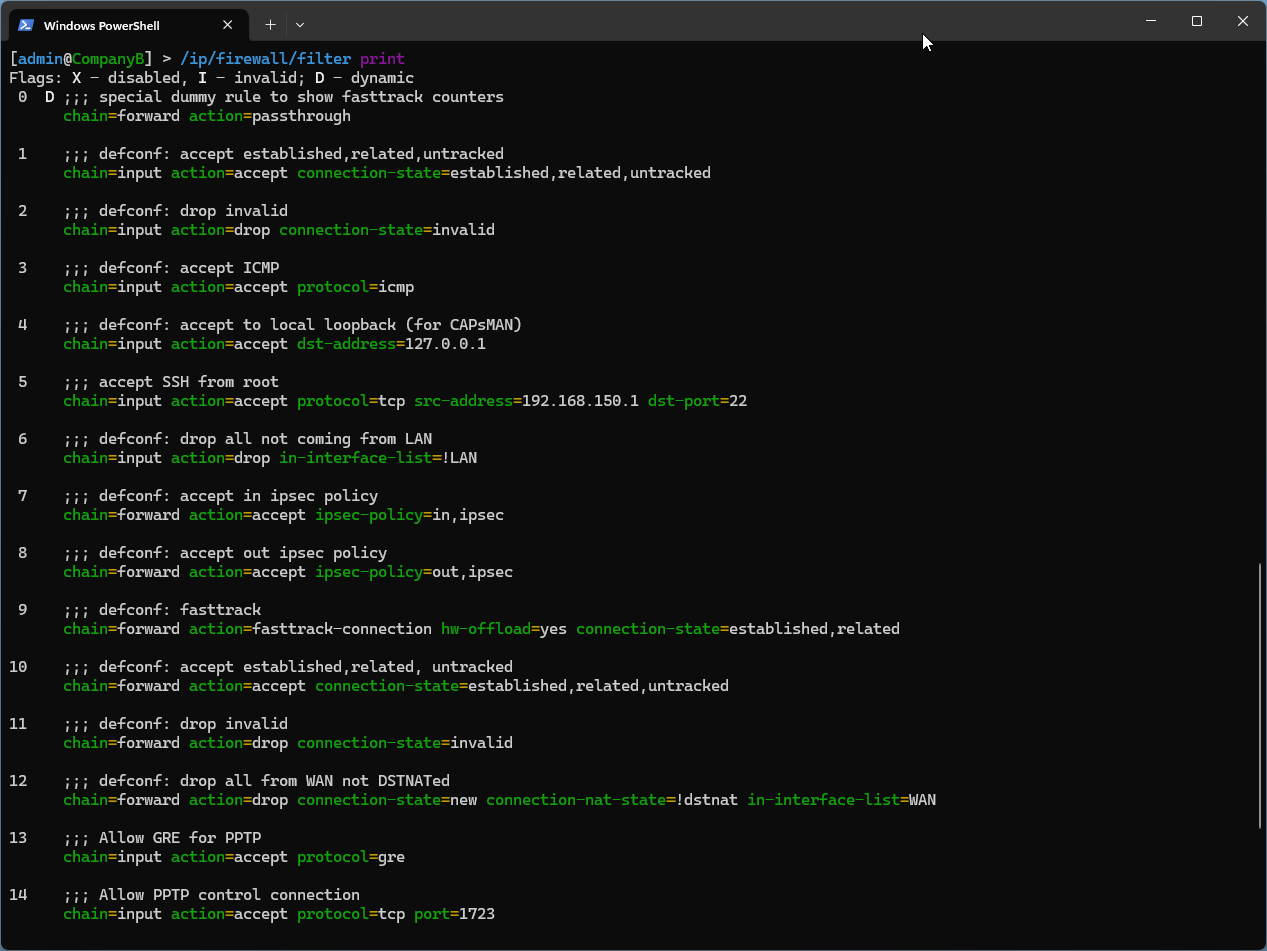
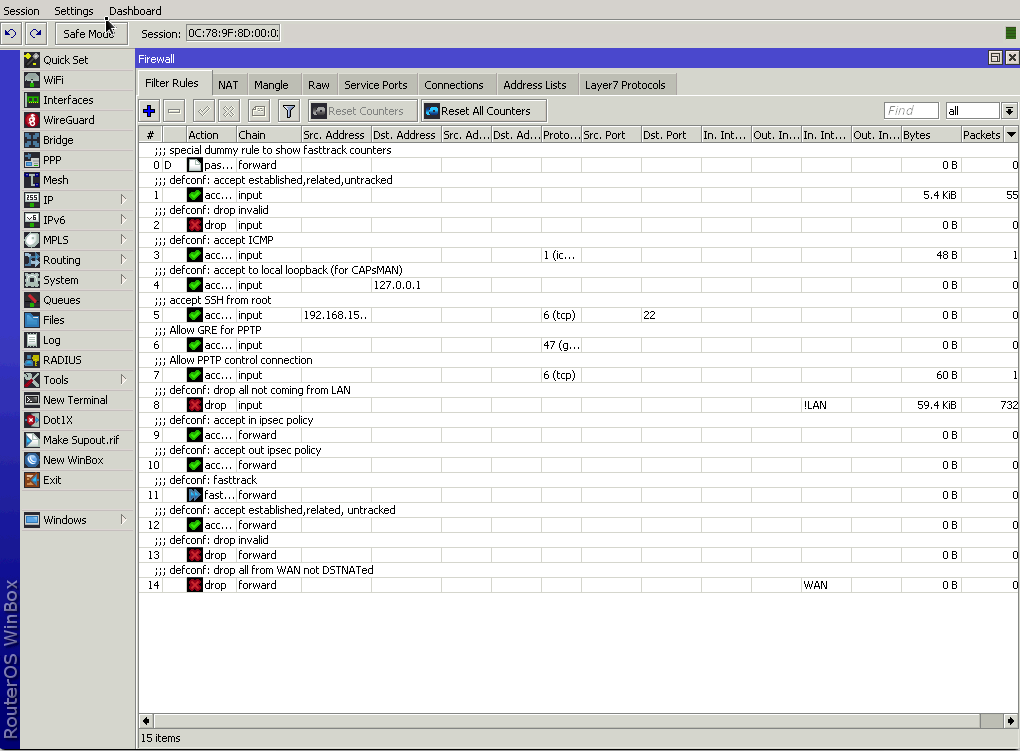
To move our new firewall rules accordingly, execute the following code.
/ip/firewall/filter move 13 6
/ip/firewall/filter move 14 7
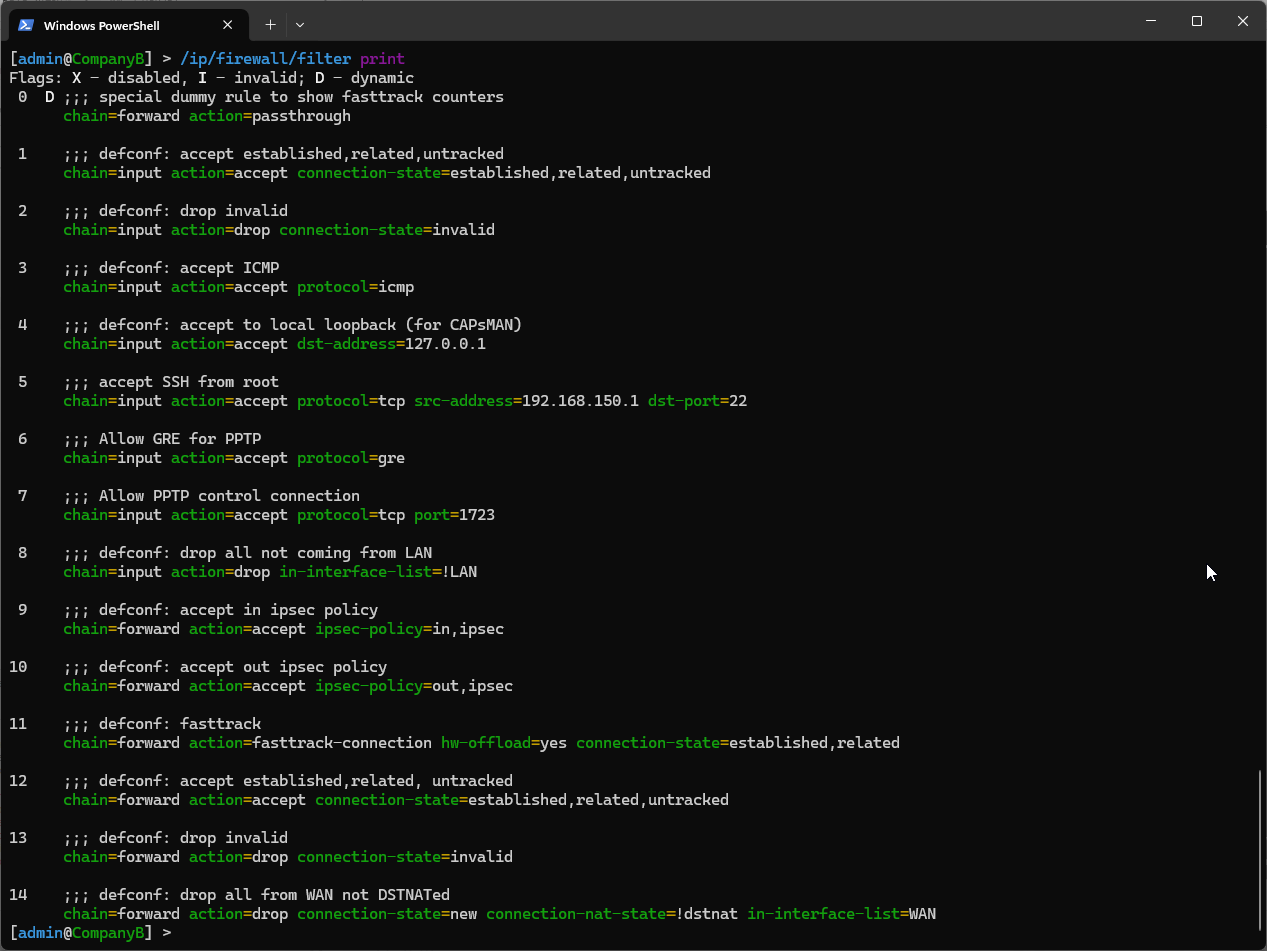
You can also create, assign, and move the firewall rules around using WinBox by going to IP -> Firewall. To move a rule, simply select the rule and drag it to its new position.
SSTP Firewall Setup
IP Firewall Changes on Company B
Generic (allow SSTP traffic from any host)
/ip firewall filter
add chain=input protocol=tcp port=443 action=accept comment="Allow SSTP traffic"
OR
Specific (allow SSTP from only Client A)
/ip firewall filter
add chain=input protocol=tcp port=443 src-address=192.168.150.146 action=accept comment="Allow SSTP from Client A"
Again, just like in the above PPTP example, we also need to move our firewall filter rule above line 6 in order for it to catch our SSTP traffic. In order to do that, we need to execute the following code: (Assuming that our new rule is #13 – please adjust accordingly if yours is not)
/ip/firewall/filter move 13 6
Benefits of Using SSTP in Relation to Firewall Rules & Why we like using SSTP
- Firewall and NAT Traversal:
- Port 443 Usage: SSTP uses port 443, which is the same port used for HTTPS traffic. This port is typically open on most firewalls and NAT devices because it is commonly used for secure web browsing. As a result, SSTP traffic can often bypass restrictive firewall rules and NAT configurations that might block other VPN protocols like PPTP or L2TP/IPsec.
- Ease of Traversal: Since port 443 is almost always open for HTTPS traffic, SSTP has a higher chance of traversing firewalls and NAT devices without requiring special configurations. This makes it particularly useful in environments with strict outbound traffic filtering or where other VPN protocols might be blocked.
- Encrypted Traffic:
- SSL/TLS Encryption: SSTP provides encryption through SSL (Secure Sockets Layer) or its successor, TLS (Transport Layer Security). This means that the VPN traffic is encrypted and secured as it is transmitted over the internet, which also helps it blend in with other HTTPS traffic.
- No Need for Additional Encryption: Since SSTP traffic is already encrypted via SSL/TLS, there's no need for additional encryption protocols like IPsec. This can simplify firewall and VPN configuration.
- Improved Security:
- Built-in Security: SSTP provides robust security features, including encryption and integrity checks, directly through its use of SSL/TLS. This enhances overall security compared to protocols like PPTP, which is considered less secure and may require additional measures like IPsec to achieve a similar level of protection.
- Simplicity in Configuration:
- Less Complicated Rules: Because SSTP traffic is often permitted by default (due to its use of port 443), network administrators may find it easier to configure firewall rules for SSTP compared to protocols that use less common ports or require additional configurations for GRE or IPsec.
- Stealth and Reliability:
- Bypass Restrictions: SSTP’s use of port 443 can help it bypass restrictive network policies and deep packet inspection (DPI) that might be used to block other VPN traffic. This can make SSTP a more reliable choice for VPN connections in restrictive environments.
Comparison with Other Protocols:
- PPTP: PPTP typically uses port 1723 for control connections and requires GRE (protocol 47) for data transfer. Firewalls may block these ports and protocols, making PPTP less reliable in restrictive environments.
- L2TP/IPsec: L2TP uses port 1701, and IPsec typically uses ports 500 and 4500. Configuring firewalls to handle these ports and protocols can be more complex compared to allowing HTTPS traffic on port 443.
L2TP/IPSec Firewall Setup
IP Firewall Changes on Company B
Generic (allow L2TP/IPSec from any client)
/ip firewall filter
add chain=input protocol=udp port=500 action=accept comment="Allow IKE (IPSec)"
add chain=input protocol=udp port=4500 action=accept comment="Allow NAT-T (IPSec)"
add chain=input protocol=ipsec-esp action=accept comment="Allow ESP (IPSec)"
add chain=input protocol=udp port=1701 action=accept comment="Allow L2TP"
OR Specific (create a specific inclusion rule for Client A)
/ip firewall filter
add chain=input protocol=udp port=500 src-address=192.168.150.146 action=accept comment="Allow IKE (IPSec)"
add chain=input protocol=udp port=4500 src-address=192.168.150.146 action=accept comment="Allow NAT-T (IPSec)"
add chain=input protocol=ipsec-esp src-address=192.168.150.146 action=accept comment="Allow ESP (IPSec)"
add chain=input protocol=udp port=1701 src-address=192.168.150.167 action=accept comment="Allow L2TP from Client A"
Again, just like in the above examples, we also need to move our firewall filter rule above line 6 in order for it to catch our SSTP traffic. In order to do that, we need to execute the following code: (Assuming that our new rules are #13-16 – please adjust accordingly if yours is not)
/ip/firewall/filter move 13 6
/ip/firewall/filter move 14 7
/ip/firewall/filter move 15 8
/ip/firewall/filter move 16 9
Definitions:
- IKE (Internet Key Exchange) sets up and manages secure connections by negotiating keys and authentication methods. IKE handles the authentication of both parties to ensure that they are who they claim to be.
- NAT-T (NAT Traversal) helps VPNs work through NAT devices by encapsulating traffic. NAT devices change the source or destination IP addresses of packets, which can interfere with VPN protocols. NAT-T encapsulates IPsec packets within UDP packets, making it easier for these packets to pass through NAT devices.
- ESP (Encapsulating Security Payload) ESP encrypts the payload of the IP packet to ensure the data is kept confidential. It also includes a cryptographic checksum to ensure the data has not been altered in transit.
- L2TP creates tunnels for transmitting data and is often paired with IPsec for secure VPN connections.
Let's look at an example on the IPSec/LT2P. To see what's going on behind the firewall, issue the following command:
/ip/firewall/connection/print
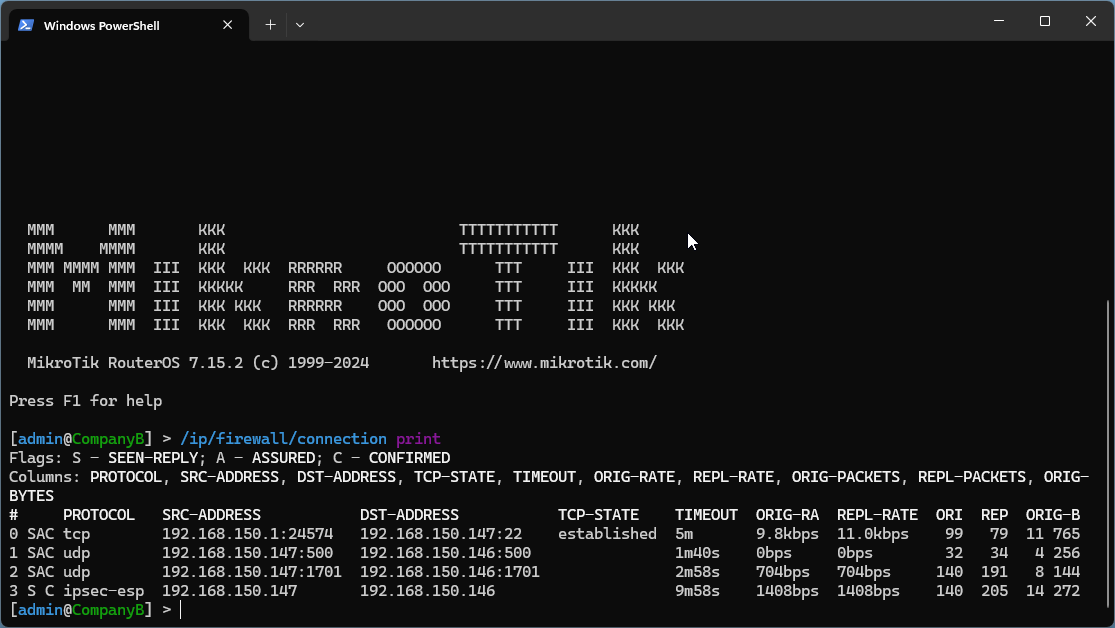
Now, from PC1, lets ping the server, and then see what happens then.
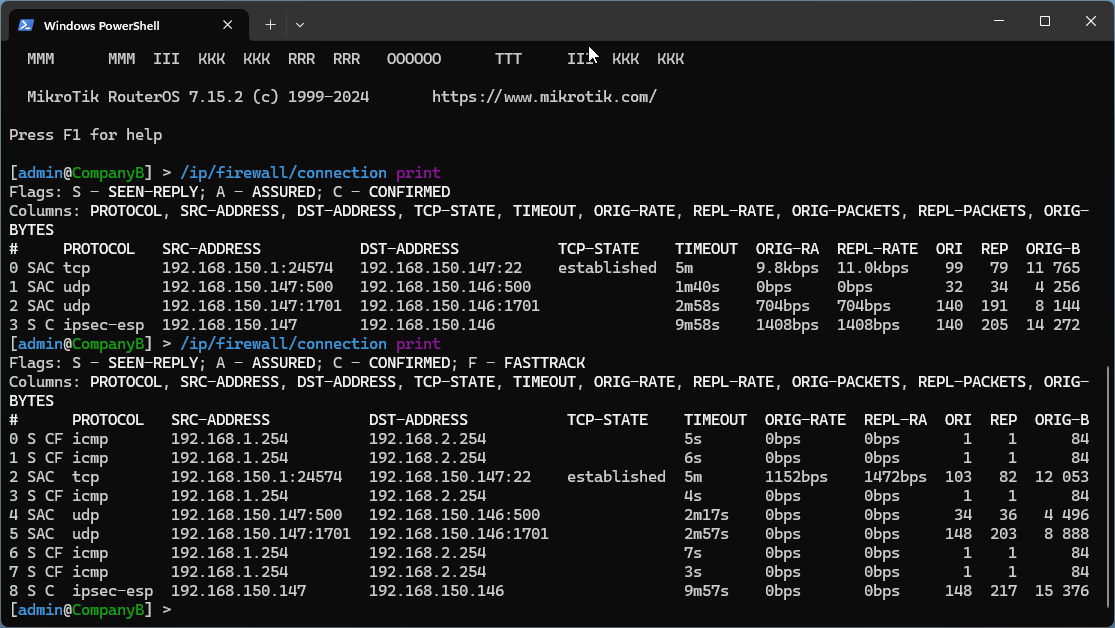
So we can see that there is both UDP traffic for the VPN and ICMP traffic from our ping.
Configuring firewall rules for VPNs is a critical step in ensuring secure remote access to network resources. By understanding connection states, implementing appropriate rules, and continuously monitoring traffic, you can create a robust security policy that protects your network while allowing authorized users to connect seamlessly.